Ech0's Laboratory
Discover our projects below.

Cybersecurity blog
Blog posts in various cybersecurity themes: malware, exploitation, reverse engineering, tips...
Polkadot validators
Discover our Polkadot ecosystem validators (master nodes)!

dotID.app - Polkadot Identity Registrar
Full Polkadot on-chain identity solution: setting, updating, clearing requesting judgement...
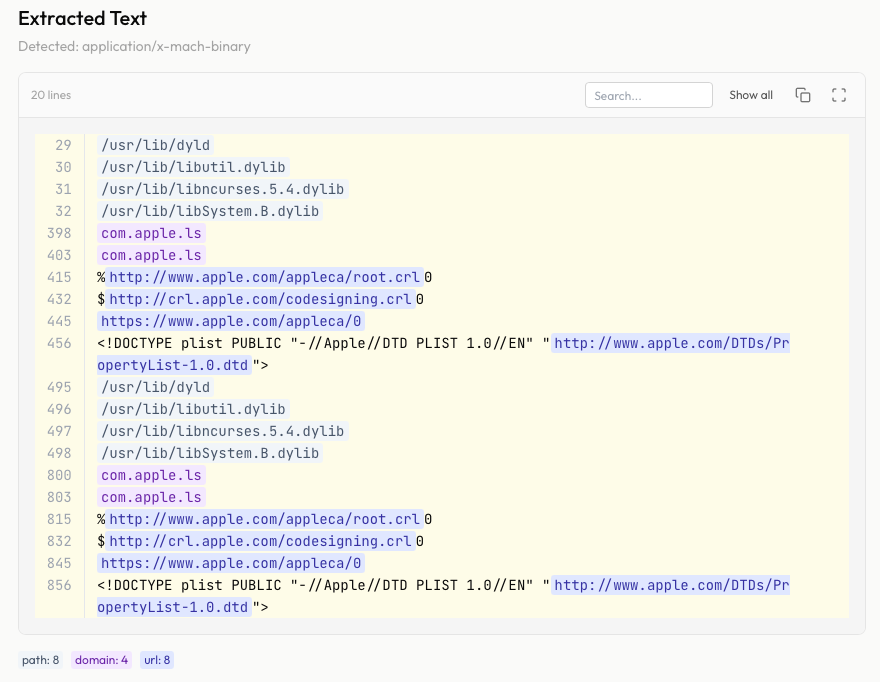
anything2text
Free online tool to extract text from any file. Supports PDF, Word, Excel, images, audio, video and 50+ formats.